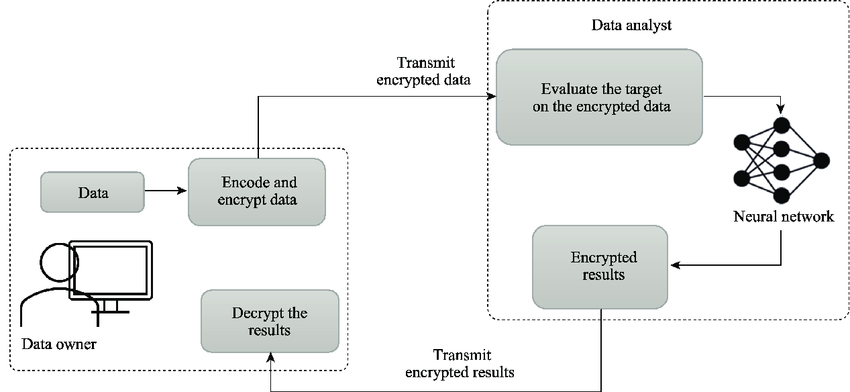
Homomorphic Encryption (HE) is a form of encryption that allows computations to be performed directly on encrypted data (ciphertexts) without needing to decrypt it first.
- The result of such a computation, when decrypted, matches the result of the same operation performed on the original plaintext.
- In simpler terms: You can “calculate with locked data,” and only the owner of the secret key can unlock the final result.
Types of Homomorphic Encryption
- Partially Homomorphic Encryption (PHE)
- Supports only one type of operation (addition OR multiplication).
- Example: RSA (multiplication), Paillier (addition).
- Somewhat Homomorphic Encryption (SHE)
- Supports limited numbers of both addition and multiplication operations before noise (errors in ciphertext) becomes too large.
- Fully Homomorphic Encryption (FHE)
- Supports unlimited additions and multiplications on encrypted data.
- Considered the “holy grail” of encryption but computationally expensive.
- First introduced by Craig Gentry in 2009.
How It Works (Simplified)
- Key Generation – A public key (for encryption) and private key (for decryption) are created.
- Encryption – Data is encrypted with the public key.
- Computation – A server or third party performs computations (e.g., addition, search, machine learning) on the encrypted data without seeing the plaintext.
- Decryption – The data owner decrypts the result with their private key to reveal the correct computation result.
Benefits for Data Privacy
- End-to-End Security: Sensitive data (like medical records, financial data, personal info) stays encrypted even while being processed.
- Confidential Outsourcing: Companies can outsource computations (e.g., cloud services) without exposing raw data.
- Regulatory Compliance: Helps meet GDPR, HIPAA, and other privacy regulations.
- Protection Against Insider Threats: Even system administrators handling encrypted datasets can’t view sensitive content.
Real-World Use Cases
- Healthcare
- Hospitals can collaborate on patient research without revealing raw medical data.
- Genomic data analysis in encrypted form.
- Finance
- Banks can run credit scoring, fraud detection, and risk assessment on encrypted customer data.
- Cloud Computing
- Users can store encrypted data in the cloud and still allow the cloud to perform searches, analytics, or machine learning.
- Government & Defense
- Secure sharing of intelligence data across agencies without exposing raw details.
- AI & Machine Learning
- Privacy-preserving AI models trained on encrypted datasets.
Challenges
- Performance Overhead: FHE is computationally heavy (1000× slower than plaintext operations, though improving).
- Implementation Complexity: Requires specialized cryptographic libraries and deep expertise.
- Noise Management: Repeated operations on ciphertext can introduce errors (noise), requiring bootstrapping techniques.
- Scalability: Still maturing for large-scale real-time systems.
Future of Homomorphic Encryption
- Active research aims to make FHE faster and more practical.
- Companies like IBM, Microsoft, Google, and Zama are developing HE libraries and tools.
- Likely to become a cornerstone of privacy-preserving computation, especially with rising demand for secure AI and data sharing.