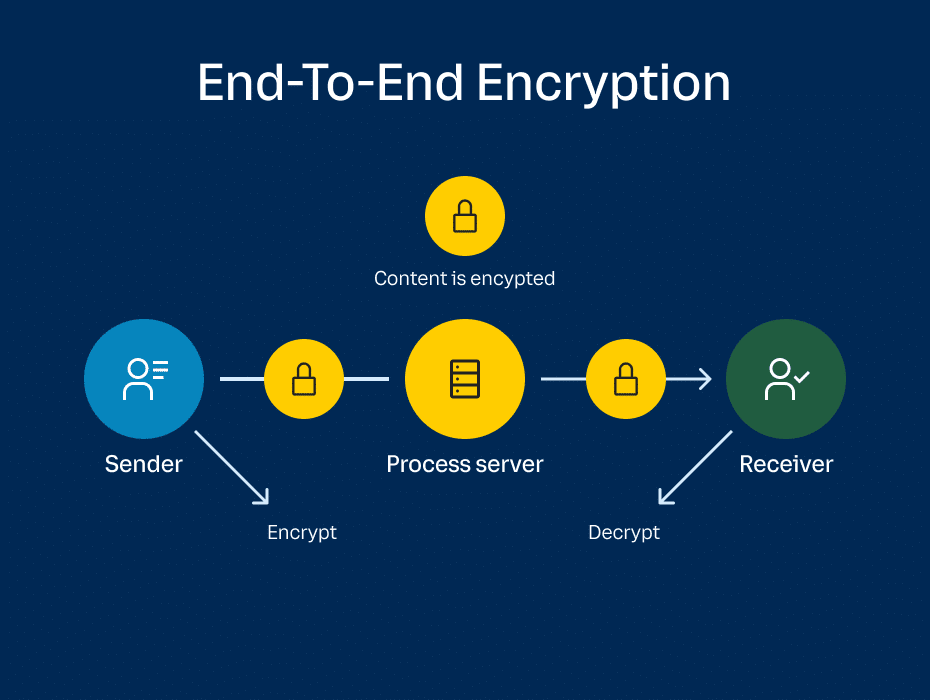
End-to-End Encryption (E2EE) ensures that only the sender and receiver of a message can read its contents — no one else, not even the service provider, government, or hackers.
The term “End-to-End Encrypted Communication 2.0” refers to the next generation of secure communication systems — enhanced with post-quantum encryption, zero-trust verification, secure metadata handling, and privacy-preserving features such as forward secrecy and multi-device synchronization without compromising encryption integrity.
In essence, E2EE 2.0 is the evolution of traditional E2EE to meet modern security challenges, including:
- Quantum computing threats
- Cloud-based and multi-device environments
- Advanced surveillance and data analytics attacks
Core Principles of End-to-End Encryption
- Message Confidentiality — Only sender and recipient can read the data.
- Integrity — The message cannot be altered in transit.
- Authentication — Both parties can verify each other’s identity.
- Forward Secrecy — Past messages remain secure even if a key is compromised.
- Post-Compromise Security — Future messages remain protected after a compromise.
How E2EE 2.0 Works (Step-by-Step)
- Key Generation:
- Each user generates a pair of cryptographic keys:
- Public key (shared with others)
- Private key (kept secret)
- Each user generates a pair of cryptographic keys:
- Key Exchange (Secure Channel Setup):
- The sender encrypts a session key using the recipient’s public key.
- Protocols like Diffie-Hellman, X3DH, or PQXDH (Post-Quantum X3DH) are used.
- Message Encryption:
- Each message is encrypted using a session key derived from shared secrets.
- Common algorithms: AES-256, ChaCha20-Poly1305, Curve25519, or Kyber (for post-quantum).
- Transmission:
- The encrypted message is sent through the server (which cannot decrypt it).
- Decryption:
- The receiver uses their private key to derive the session key and decrypt the message.
Key Technologies in E2EE 2.0
1. Post-Quantum Cryptography (PQC)
Quantum computers can break classical encryption (like RSA and ECC).
E2EE 2.0 integrates quantum-resistant algorithms such as:
- Kyber (key exchange)
- Dilithium (digital signatures)
- Falcon
- SPHINCS+
2. Double Ratchet Algorithm
Used by Signal, WhatsApp, and others — ensures forward and backward secrecy by changing keys after every message.
3. Multi-Device Encryption
E2EE 2.0 introduces secure synchronization across multiple devices (phones, laptops, tablets) while maintaining encryption:
- Uses secure backup encryption keys
- Employs device-specific subkeys
4. Secure Metadata Protection
While older E2EE systems exposed metadata (sender, time, size), E2EE 2.0 includes:
- Metadata-hiding networks (like Tor, mixnets)
- Private Information Retrieval (PIR) protocols
- Oblivious relay systems
5. Zero-Trust Architecture Integration
E2EE 2.0 aligns with Zero Trust principles — assume no device or server is inherently safe.
- Each device re-authenticates using cryptographic proofs.
- No trusted intermediaries are required.
6. Decentralized Identity (DID) & Blockchain
Blockchain or DID systems allow verifiable user identities without revealing personal data.
Used for:
- Secure contact discovery
- Revocation lists
- Auditability of key changes
E2EE 2.0 in Action (Examples)
| Platform | Encryption Type | Unique Feature |
|---|---|---|
| Signal | Double Ratchet + X3DH | Metadata minimization |
| Signal Protocol | Multi-device E2EE | |
| Matrix (Element) | Olm/Megolm + PQC trials | Open-source E2EE 2.0 |
| ProtonMail / ProtonDrive | E2EE + Zero-Access Architecture | End-to-end email & file encryption |
| Apple iMessage (PQ beta) | PQC integration (Kyber) | Post-quantum protection for iCloud |
Applications of End-to-End Encrypted Communication 2.0
- Secure Messaging Apps (Signal, Telegram Secret Chats, WhatsApp)
- Encrypted Email Platforms (ProtonMail, Tutanota)
- Video Conferencing Tools (Zoom E2EE, Microsoft Teams Secure Mode)
- Healthcare Data Exchange
- Cloud Storage (ProtonDrive, Tresorit, Sync.com)
- Financial Transactions & FinTech Apps
- Government and Military Communications
- IoT and Smart Device Communication
- Remote Work Collaboration Platforms
- Social Media & Metaverse Privacy Layers
Advantages of E2EE 2.0
- 🔒 Quantum-safe encryption
- 🌍 Secure cross-device communication
- 🕵️♂️ Privacy-respecting metadata handling
- 🧩 Zero-trust and decentralized verification
- 🔁 Forward and backward secrecy
- 📱 Seamless usability with modern UX
Challenges and Limitations
- Complex Key Management
- Multi-device syncing increases key-handling complexity.
- Legal & Regulatory Pressure
- Governments seek “lawful access” (which undermines E2EE).
- Metadata Leakage
- Even advanced E2EE may expose behavioral patterns.
- Quantum Threats Still Emerging
- PQC algorithms are still under evaluation for performance and standardization (NIST PQC 2024).
- Performance Overhead
- Post-quantum algorithms may increase computational and bandwidth requirements.
The Future of Encrypted Communication (E2EE 3.0 Preview)
Next-generation encryption will include:
- Quantum Key Distribution (QKD) over optical fiber or satellite
- Homomorphic Encryption (processing encrypted data)
- Federated Secure Messaging Networks
- AI-powered intrusion and anomaly detection within encrypted networks
- Interoperability between E2EE apps under unified standards (IETF MLS Protocol)
Summary
| Feature | E2EE 1.0 | E2EE 2.0 |
|---|---|---|
| Encryption Type | Classical (RSA, ECC) | Post-Quantum (Kyber, Dilithium) |
| Security Focus | Message confidentiality | Metadata + Quantum security |
| Architecture | Centralized | Zero-trust, decentralized |
| Device Support | Single device | Multi-device synchronized |
| Future-readiness | Limited | Quantum and AI ready |